Consider the scenario where you're configuring a proof of concept 11g implementation using Oracle Internet Directory as the authentication provider. Oracle's Fusion Middleware Security Guide for 11g certainly provides you with a bird's eye view of how to configure OBIEE 11g to integrate with web logic's OID LDAP authentication provider but in this how-to I will digress slightly and present a detailed, step by step guide on how to configure your OBIEE 11.1.1.6 system to use OID LDAP authentication for users.
This how-to is a culmination of the countless posts on Oracle Technical Network requesting additional help with implementation and will provide the user answers to the most common OBI and OVD (Oracle Virtual Directory) errors that you typically encounter in this proces, including: OVD-40666, OBI-SEC-00022, OBI-SEC-00015, and LDAP error code 32.
At the end of this how-to, any user within OID will be able to log into OBIEE 11g Answers.
Note that if you're using OID as the authentication provider but storing groups in an external database table, this also serves as a suitable 'step 1' prior to implementing the groups authentication model (to be covered at a later date)
Prequisities:
Your Oracle Internet Directory must have the following users:
- BISystemUser
- BIAuthor
- BIConsumer
- BIAdministrator
These are out-of-the-box weblogic users that weblogic uses in its defaultauthenticator for users, groups, and application roles.
If you are using Oracle Internet Directory to store groups, then it must include the following weblogic out of the box groups:
- BIAdministrators
- BISystemUsers
- BIAuthors
- BIConsumers
Step 1: Add Oracle Internet Directory as an Authentication Provider in Weblogic Administration Console
1.a) Navigate to Security Realm -> myRealm -> Providers -> Authentication -> New
to add an OID Authentication Provider
* Note that at this point, you will not see myOIDDirecotory in your Authentication Provider. You will be adding this authentication provider in the next steps. Your only two authentication providers should be: DefaultAuthenticator and DefaultIdentityAsserter
1.b) After Clicking 'New', populate the 'Create a new Authentication Provider' screen as outlined below:
1.c.) After clicking 'Ok' Your myOIDDirectory Authenticator Provider will appear on the Authentication Provider list below: Click 'myOIDDirectory' to begin the configuratin of the Provider Specific information:
Step 2: Configure the myOIDDirectory Authentication Provider with required connection details
2.a) After clicking 'myOIDDirectory' navigate to 'Configuration' -> Provider Specific as seen below:
The correct configuration of Host, Port, Principal, and Credential is required before proceeding to step 2.b.. If you are unfamiliar with Oracle Internet Directory, it is recommended that consult your OID Administrator for assistance. Here is a breakdown of each required field.
Host is the ip address of your company's OID LDAP server.
Port represents the port number that the OID LDAP server utilizes for listening & communication
Principal represents the distinguished name (DN) or 'orcladmin' account needed to connect the OID LDAP server. Yes that is correct, you will need a cn=orcladmin or equivilent account for communication to the OID LDAP server. We have tested leaving the Principal and Credential field blank even if anonymous binding is enabled, with no success.
Your principal DN should represent the full path to the orcladmin account and not just cn=orcladmin.
For example: If your cn=orcladmin (or equivilant) account is under :
cn=Users,dc=trusted,dc=oracle,dc=com
Then the above Principal DN should be : cn=orcladmin,cn=Users,dc=trusted,dc=oracle,dc=com . It is not sufficient to only include cn=orcladmin
Credential/Confirm Credential represents the password of the cn=orcladmin (or equivalent) account.
Failure to correctly configure the host/port/prinicpal settings will most likely result in one of the following errors:
- OBI-SEC-00004 Unable to initialize oracle.bi.security.service.SecurityWebService
- OVD-60024 Connection error: [LDAP: error code 49 - Invalid Credentials].
- OBI-SEC-00028 System User could not be authenticated
- OBI-SEC-00003 OVD-60143 Unable to create connection to ldap://
2.b) Configure remaining required settings
User Base DN represents the OID tree branch path that stores the users .
NOTE: Here is where many people misconfigure their OID Authentication Provider in web logic. Oracle's Fusion Middleware Security Guide does not explicitly state this, but your User Base DN needs to be 1 level higher than the tree branch which stores your user list.
For example:
If your OID that contains your users is: cn=Users,dc=trusted,dc=oracle,dc=com , then your User Base DN needs to be: dc=trusted,dc=oracle,dc=com.
Failure to appropriately configure this step will result in OBI-SEC-00022 error:
SecurityService::authenticateUserWithLanguage [OBI-SEC-00022] Identity found <username> but could not be authenticated
which means that Oracle was able to find the user in the web logic console under 'Users and Groups' but could not complete the authentication against OID.
User Name Attribute specifies the OID attribute which you want to use to authentication. If you want to use the user's email address, the User Name attribute would be mail. In this example, I will use the common name (cn) .
User Object Class specifies the tree branch in OID that contains the users. Out of the box OID implementation uses 'person' , but in this example i've used a custom 'Staff tree'.
Group Base DN represents the OID tree branch path that stores the groups. Similar to User Base DN, it should be 1 level higher than the tree branch which stores your groups list. If you are using an external database table to store groups, than you can disregard this field.
Step 3: Configure the authentication control flag to sufficient
After clicking saving on 'Settings for myOIDDirectory' page, you should be back at:
3.a) Click 'myOIDDirectory' then Configuration -> Common and change the Control Flag to 'SUFFICIENT'
A SUFFICIENT control flag indicates that if the user successfully authenticates against this provider, then weblogic will release control back to the system. But if the user fails to authenticate with this provider, weblogic will continue down the authentication provider list.
Step 4: Reorganize the authentication provider list
After clicking Save on the 'Common' tab of the Settings for myOIDDirectory, you will be back in the Authentication tab. Click 'reorder' and move myOIDDirectory to the top of the list.
and then...
4.a) After clicking 'OK' you will be taken back to the Authentication tab. Click 'Activate Changes' within the Change Center, then reboot the Admin Server & BI Service.
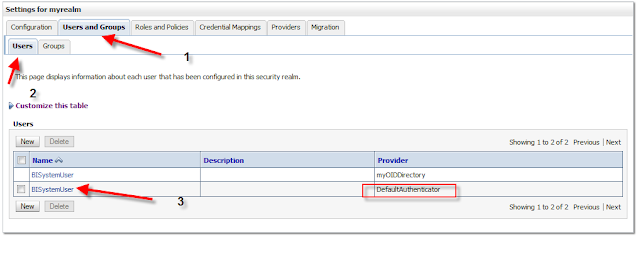
Step 5: Validate your OID users are found in the 'Users and Groups' tab
After rebooting the Admin Server and BI Service you should be able to see the Users and Groups of your OID LDAP server within the Users and Groups tab under: Security Realms -> myrealms -> Users and Groups
You should also test Groups by clicking on a user within your OID directory (for example cookjr@c02) and then viewing the groups tab:
Even if you are using an external database table to store groups (and not OID), clicking on groups for a specific user should not return an error.
"If your users do not appear on the Users and Groups tab, or viewing the groups of a specific OID user throws an error, do not proceed to step 6 and instead, review your configuration settings with your OID Administrator"
Step 6: Fusion Middleware Changes
At this stage, we are going to move to Fusion Middleware to make the required application role changes. I've decided to seperate that into
part 2 which you can find here
keywords: obiee 11g authentication, ldap authentication, weblogic authentication provider, obiee 11g oid authentication, custom authentication provider